I've got a new paper accepted at CHES, to be published in TCHES 2026/1 around beginning of December and out on eprint now. The topic of the paper is a way of monitoring a tamper-sensing mesh through time-domain reflectometry using very cheap components. The end result is a circuit that costs about 10 € in parts that is able to measure TDR responses with a few hundred picoseconds of resolution.
Tamper-Sensing meshes are squiggly circuit traces that are used to tamper-proof high-security devices like hardware security modules, ATM pin pads and countertop card payment terminals. Any area where you would like to prevent an attacker from drilling or sawing through in a physical attack, you completely cover with one or more such circuit traces in a meandering pattern. I've written up some work on a KiCad plugin for creating these meshes in another post.
Up to now, the state of the art in monitoring these security meshes has mostly been finding ways to precisely monitor their ohmic resistance in the analog domain. This has the disadvantage of both being fairly complex in circuitry and of presenting a steep trade-off between sensitivity and false-positive rate since all you get out of the whole mesh is a single analog measurement containing maybe 12 to 16 bits of entropy. There have been a few papers on using more advanced RF techniques, but they all either required really expensive circuitry and/or highly customized meshes that for instance couldn't easily be fitted into arbitrary shapes.

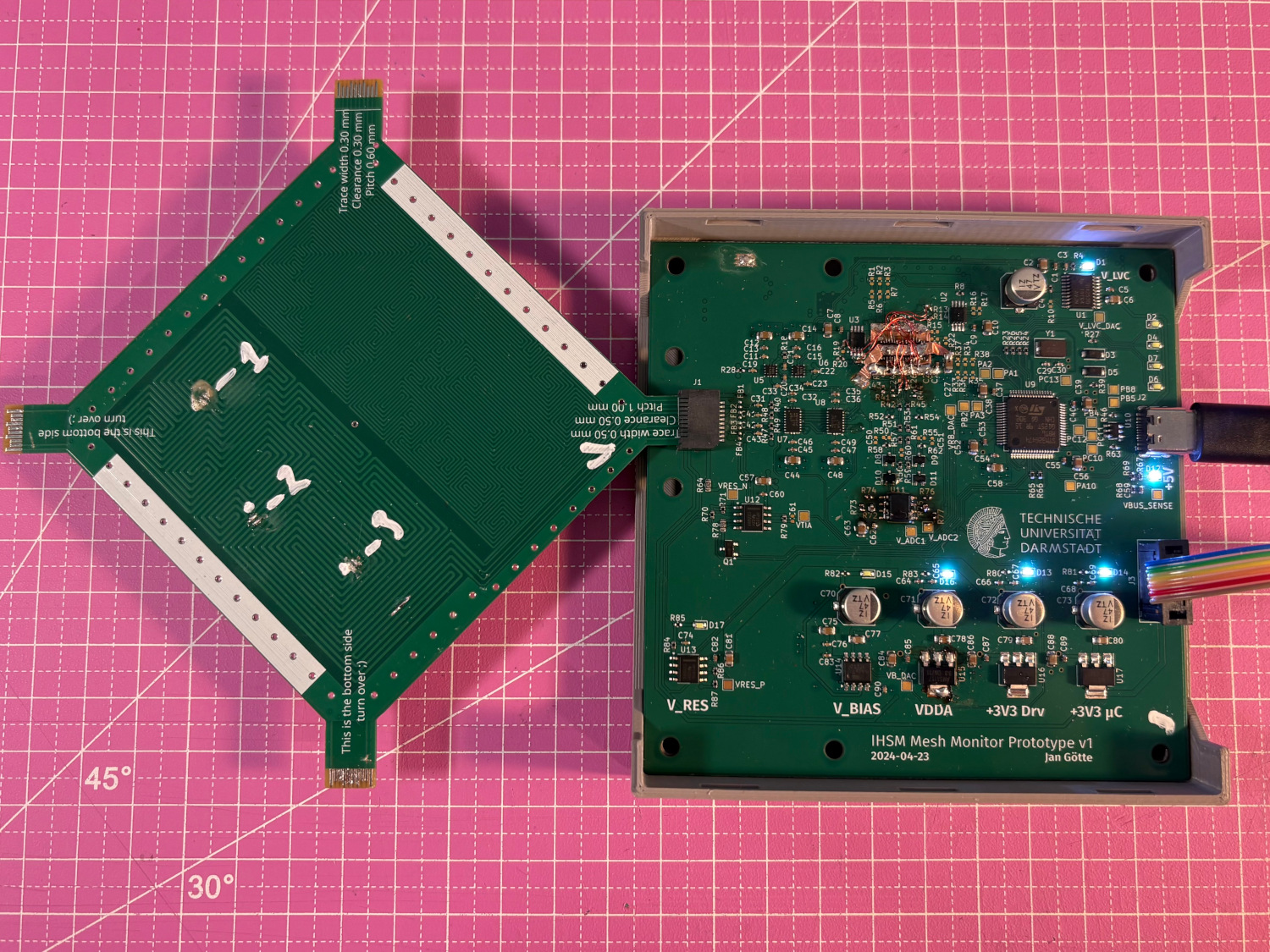
In this paper, I wrote up a method using the high-resolution timer of an inexpensive STM32G4-series microcontroller together with a DisplayPort/HDMI "redriver" chips meant for amplifying high-speed display signals to create fast pulse edges. I characterized several chips, with the best performers being TI's TDP0604 and Diodes' PI3HDX12211, coming in at 2 to 5 € depending on where and how much you buy. The fast edges generated by these drivers are then fed to a set of four-diode sampling gates using cheap RF schottky diodes to create a really cheap but fast time-domain reflectometer. Using this TDRD circuit, a security mesh can be monitored much more precisely than before, since the circuit creates a sort of fingerprint of the mesh's trace along its length.
One of the fun highlights of this project to me was micro-soldering test boards using different redriver ICs. Above, you can see the result of that soldering work. I was really happy with my cheap aliexpress microscope and with my fancy titanium tweezers!
Have a look into the paper, where I wrote up details on the circuitry as well as a whole bunch of (>1000!) measurements characterizing the system. As it turns out, it's really sensitive to attacks while being reasonably robust to environmental disturbances. In fact, it's so sensitive that the circuit can distinguish multiple identical (!) copies of the same mesh produces by JLCPCB from their manufacturing tolerances such as FR-4 fiber weave alignment.
You can find a preprint of the paper on eprint, and I'll update this post with a link to the published version of the paper when it becomes available. The eprint is identical to the published version as of now.
The source code of the project is available at https://git.jaseg.de/sampling-mesh-monitor.git.